GitHub’s token-scanning feature, which carefully monitors repositories for nefarious code injection, is adding Dropbox, Discord, Atlassian, Proctorio, and Pulumi as partners in an effort to broaden its understanding of what a ‘bad’ token is.
The token-scanning feature was launched last year alongside GitHub Actions, a method for stringing together automation within your repos. Actions has since broadened its scope to encompass CI/CD.
Token scanning acts as a sort of clearinghouse for auth security on the platform. Its aim is to help unwitting participants from carrying injected code with them around the internet, or avoid allowing authorization to the wrong entity. You may weave a repo into your own work without realizing it’s carrying some form of spyware; the person or people who created that repo/library may not be aware, either. Code injection often happens in pull requests, and it’s not always easy to spot tiny bits of malicious code.
Similarly, busy projects may be authorizing users without carefully checking to see who they are. If a problem is spotted, GitHub sends the manager of a repo a request to authorize the token.
One vulnerability with token scanning: It uses “known formats.” Prior to adding the aforementioned partners, GitHub was limited to the formats it was aware of. While GitHub was aware of many (it also says its token-scanning feature has sent over one billion tokens to users for validation), there was room to do better. Adding Dropbox, Discord, Atlassian, Proctorio, and Pulumi as partners keeps the program growing.
GitHub already partners with Alibaba Cloud, AWS, Azure, Google Cloud, Mailgun, npm, Slack, Stripe, and Twilio for token scanning. Each partner will contribute to the token ‘knowledge base’ to keep repos secure.
Like GitHub, Twilio Armors Up
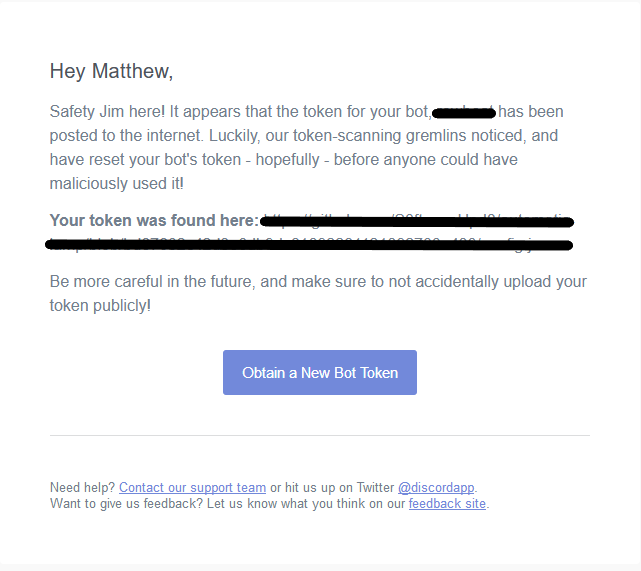
Sometimes an authorization code is simply compromised, as was the case with one Discord bot:
Twilio, like Discord, is being proactive about leaked authorization tokens. Its new Git Guard feature tells you if your Twilio Account SID and Auth Token were committed to a public repository, no matter how purposeful that was.
Token scanning is a handy safety net, and in a time when security is at its most fraught (and inarguably vital) it’s nice to know the companies we trust most with our data are making efforts to help us keep it safe.



